Vault Management = Risk Management
If you manage the vault, you manage the risk.
The first generation of vaults was simple by design. Users deposited an asset and selected a strategy. A smart contract deployed the asset and issued a yield token. An auto-compounder farmed LP rewards on a DEX/AMM.
That era is over.
Vaults have evolved into structured products with complex, multi-leg strategies combining:
- Perps, basis trades, and options overlays
- Leveraged lending loops
- Positions in other structured strategies
- Re-hypothecated collateral
- Re-staking and RWA exposure
At this level of complexity, a vault is no longer a yield product; it becomes a risk container. In this article, we outline our approach to vault risk management, identify current sources of systemic fragility, and highlight how the limited use of data-driven frameworks introduces unnecessary risk in today’s vault designs.
Understanding Vault Risk

An onchain vault can be mapped across three risk axes: solvency risk, liquidity risk, and yield volatility risk. Other risks exist, but they collapse into one of these categories.
- Solvency risk is the risk that a vault cannot fulfill its liabilities to depositors without imposing a permanent principal loss. This occurs when asset values materially change and no longer cover claims. Solvency risk also appears when collateral fundamentally depegs but does not liquidate, either because liquidity is insufficient or hardcoded oracles are misused.
- Liquidity risk concerns when and how users can withdraw funds. A vault can be solvent on paper and unusable if redemptions are gated, queued for weeks, or users are forced to absorb higher than normal slippage. Liquidity risk arises from allocating into thin markets, from unbalanced risk parameters that favor excessive utilization for extended periods, or from venues with long lockups.
- Yield volatility risk measures the stability of a vault’s returns over time. Depositors tend to plan around an expected yield range. Given this requirement, a stable and predictable yield is more valuable than a higher yield that fluctuates unpredictably.
A vault must operate under a mandate that defines tolerances across these axes. Translating this into practice requires explicit operational thresholds:
What drawdown is acceptable under stress? What liquidity level must be consistently available? What yield variability can be tolerated? Which assets, oracles, and venues are within or outside the mandate?
The Chaos Framework

Defining the mandate is a starting point, execution is the actual work. As technical risk managers, we structure our approach around three pillars:
- Due Diligence: Every protocol, asset, parameter, and oracle is thoroughly reviewed and assessed. Each dependency is mapped as an exposure vector, analyzed for how it could fail and affect solvency, liquidity, and yield, and constrained with appropriate criteria and limits.
- Automated Risk Monitoring is essential when live conditions diverge from the parameter assumptions set at launch. We deploy Chaos Risk Oracles to surface the signals that trigger automatic actions such as limiting new inflows, tightening or pausing markets, adjusting collateral parameters, or applying allocation constraints to preserve solvency and liquidity. The aim is for consistent adherence to the vault’s mandate without relying on manual oversight.
- Optimized Allocation: We recommend vault allocations modeled to balance yield, liquidity, and stability. Rather than chasing the highest APY, we recommend optimizing within defined constraints: expected returns, acceptable drawdowns, exit liquidity, and yield variability. A core principle is that curators should not rely on solvency risk for returns. If a strategy only appears attractive because it shifts unbounded tail risk onto depositors, it does not belong in the vault.
Lessons from the Market
The last few weeks have been a live stress test for DeFi’s yield-product architecture.
Stream, Elixir, Stables Labs’ USDX, and Moonwell may look like separate events. Underneath, they follow the same pattern: complex risk containers with limited risk management.
- Stream and Elixir were both solvency and liquidity-related, turning the collapse of a relatively small asset into a system-wide problem. Stream had roughly $162M in assets before its failure, yet poor risk management amplified this damage across multiple protocols and curators.
- USDX’s depeg highlighted the importance of mapping dependencies and maintaining risk controls that respond to edge-case scenarios, such as extreme volatility across underlying assets, venue-level disruptions, or a Balancer-style liquidity failure. Note that all delta-neutral strategies rely on a complex web of venues, assets, and assumptions that can be stressed simultaneously. They remain “neutral” only when that entire dependency graph is understood and protected.
- Moonwell highlighted the oracle dimension and dependency. A single bad data path led to over $1M in lost funds.
In each case, the issue was not with the fundamental design of the protocol or strategy, but with its risk management and profile. The Chaos framework closes this gap by mapping dependencies early, monitoring live conditions with risk-aware oracles, and enforcing allocation limits that hold when markets come under stress.
When Price Becomes a Risk Surface
Crypto oracles began as price feeds or data pipelines.
As complexity increased, price and risk converged, and the oracle layer has to evolve into an intelligence layer. Risk Oracles surface the state of an asset across liquidity, volatility, utilization, reserves, and other signals. This information can be compared directly against a vault’s mandate, making the oracle a core part of the risk framework rather than a passive data source.
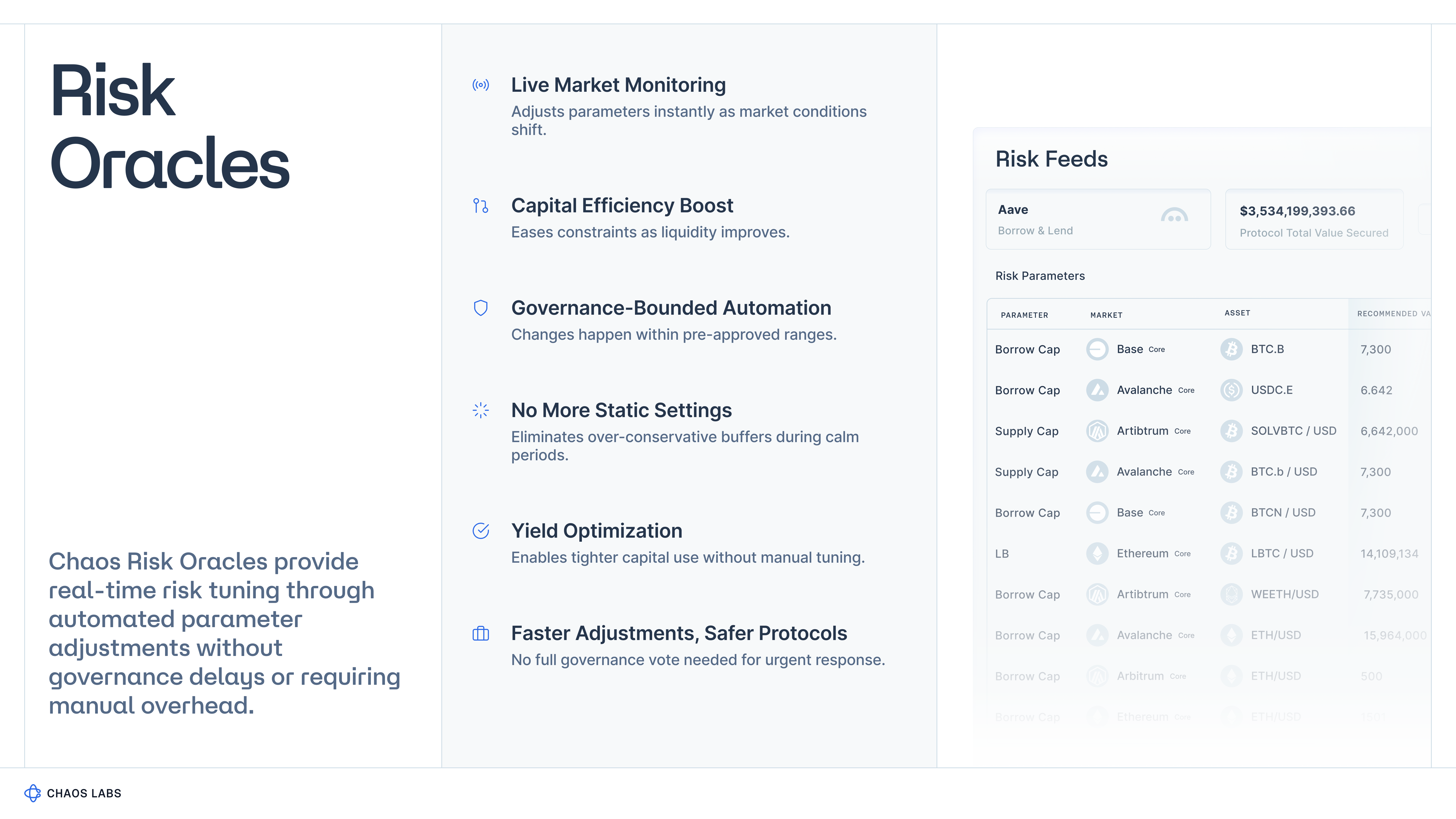
For a vault, this turns a static configuration into a dynamic control system. Parameters such as caps, LTVs, venue limits, and allocation weights are no longer fixed numbers in a spreadsheet that require manual adjustments; instead, they can adapt when risk conditions change. When volatility spikes, liquidity thins out, or reserves deteriorate, Risk Oracles can trigger the logic that pauses flows, limits new exposure, or rebalances to keep the vault within its defined tolerances.
Conclusion
Vaults are no longer farming strategy wrappers.
They’ve evolved into structured products wired through multiple protocols, assets, venues, and oracles. This makes them risk containers by definition. Viewed through a risk management lens, the recent wave of incidents is not surprising. The path forward is not to make vaults less ambitious but to make their risk management modern and enforceable:
- Define a mandate across the core risk axes (solvency, liquidity, yield volatility)
- Run real due diligence on every protocol, asset, parameter, and oracle in the dependency graph
- Use automation to keep the live system inside those bounds
- Allocate in ways that do not rely on solvency risk as a hidden source of yield
The next generation of vaults will be defined less by the yield they advertise and more by how clearly (and credibly) they answer these questions.
Proof of Reserves: A DeFi Primer
When protocols treat pegged assets as risk-free collateral, solvency cannot be a hidden assumption. It must be an observable input.
A UX Framework for Onchain Lending Products
Onchain lending is a core component of crypto’s market infrastructure, and the user experience it delivers is determined by structural choices that shape how risk, liquidity, and incentives behave under stress.
Risk Less.
Know More.
Get priority access to the most powerful financial intelligence tool on the market.